In the rapidly evolving landscape of artificial intelligence (AI), cybersecurity has become a paramount concern. As of October 2025, AI technologies are deeply integrated into business operations, from predictive analytics to autonomous systems, but this integration has opened new avenues for cyber threats. According to recent reports, AI-powered attacks have surged, becoming the top concern for Chief Information Security Officers (CISOs), with a 19-point increase in priority over the previous year. Threat actors, including nation-states like Russia, China, and Iran, are leveraging AI to launch sophisticated cyberattacks targeting critical infrastructure and spreading disinformation. These developments underscore the dual-edged nature of AI: a powerful tool for innovation and a potent weapon for malice.
The rise of generative AI, such as models capable of creating deepfakes and automated phishing campaigns, has lowered barriers for cybercriminals. Criminals with minimal technical skills can now orchestrate complex operations, amplifying risks like ransomware, infostealers, and cloud vulnerabilities. For AI projects specifically, vulnerabilities extend beyond traditional IT systems. Data poisoning, where adversaries tamper with training datasets to manipulate model outputs and model inversion attacks, which reverse-engineer sensitive information from AI models, are increasingly common. These threats not only compromise project integrity but also erode trust in AI-driven decisions.
Protecting AI projects requires a proactive, multifaceted approach. Organizations must embed security into the AI lifecycle, from data collection to deployment. This article explores key cybersecurity threats in AI, their implications for projects and actionable strategies to safeguard them. By understanding these risks and implementing robust defenses, developers and businesses can harness AI’s potential while minimizing vulnerabilities. As AI adoption accelerates—with 90% of companies lacking maturity to counter AI-enabled threats—staying ahead is not optional but essential. We’ll draw on insights from industry reports and expert analyses to provide a comprehensive guide.
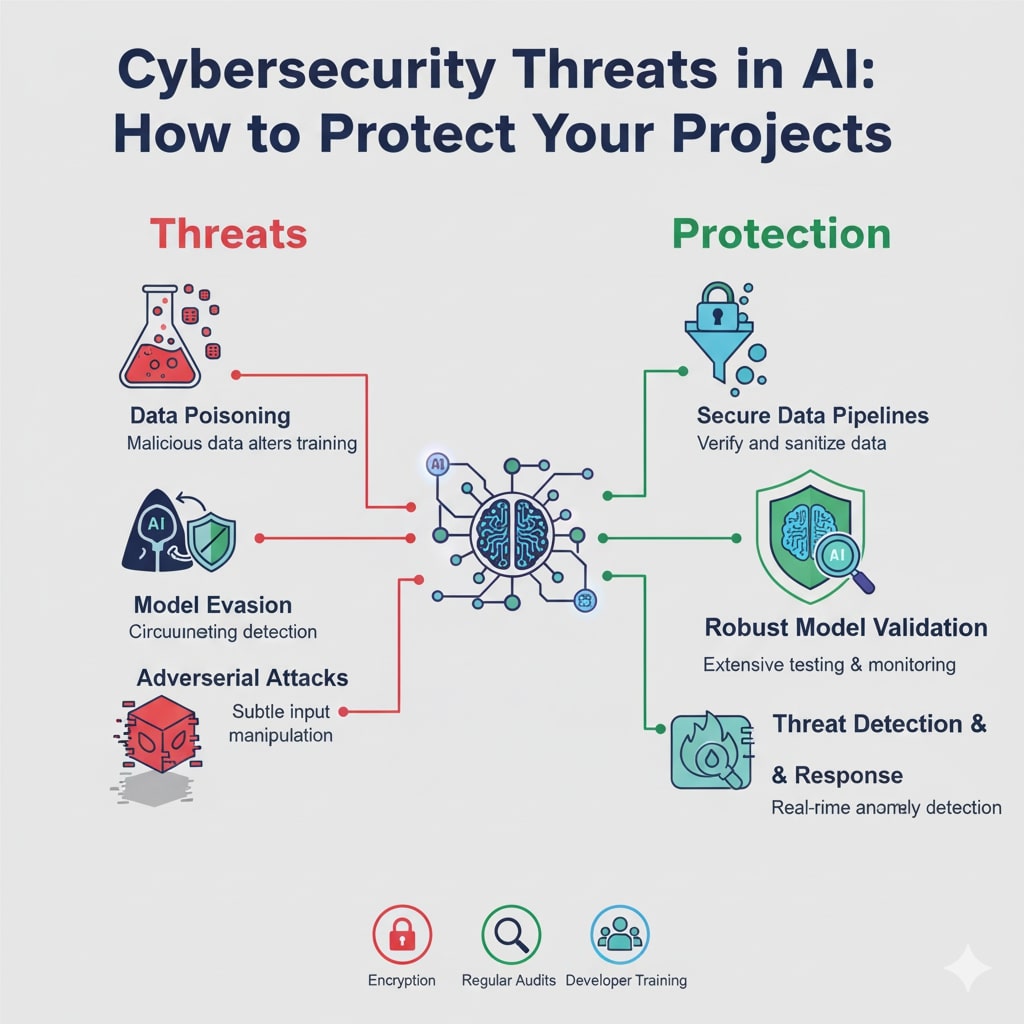
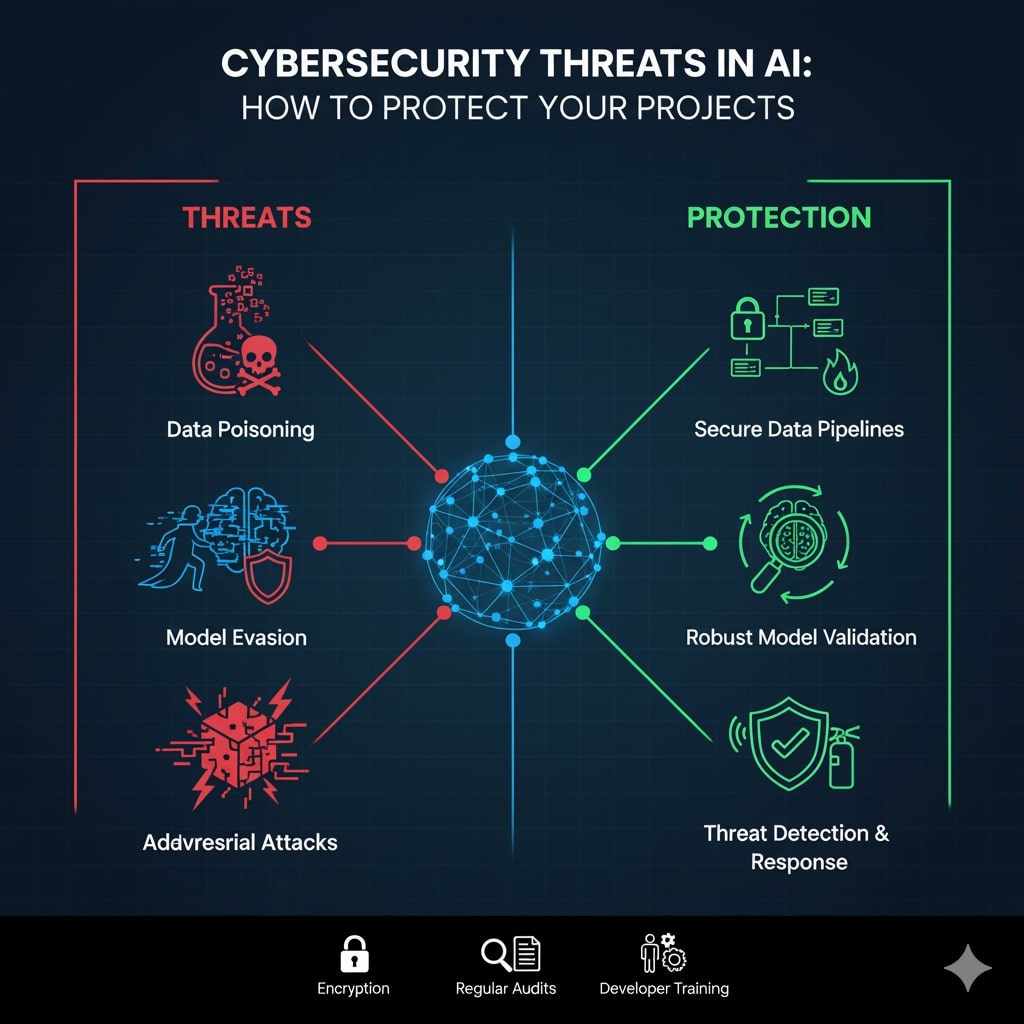
Emerging Cybersecurity Threats in AI
The intersection of AI and cybersecurity has birthed a new era of threats, where AI is both the target and the enabler of attacks. In 2025, adversarial AI techniques are at the forefront, allowing attackers to exploit systems at unprecedented speed and scale. One prominent threat is data poisoning, where malicious actors inject corrupted data into training sets, causing AI models to produce erroneous or biased outputs. This can have devastating effects in sectors like healthcare or finance, where decisions rely on model accuracy. For instance, poisoned models might misdiagnose diseases or approve fraudulent transactions, leading to financial losses or safety risks.
Another critical threat is adversarial attacks, which involve crafting inputs designed to fool AI systems. These “adversarial examples” can trick image recognition models into misclassifying objects—imagine an autonomous vehicle mistaking a stop sign for a speed limit indicator due to subtle pixel manipulations. Such attacks are evolving with AI’s help, as generative tools automate the creation of these deceptive inputs.
Model theft and inversion attacks pose intellectual property risks. Model theft involves stealing proprietary AI algorithms, often through supply chain vulnerabilities or insider threats. Inversion attacks go further by querying a model to reconstruct its training data, potentially exposing sensitive information like personal data used in training. With AI models becoming valuable assets, these thefts can undermine competitive advantages.
AI is also weaponized by cybercriminals. Deepfakes, powered by generative AI, are used for social engineering, such as impersonating executives in video calls to authorize fraudulent transfers. Nation-state actors employ AI for disinformation campaigns, amplifying fake news or manipulating public opinion. Ransomware has become more sophisticated, with AI optimizing encryption and evasion techniques. Cloud vulnerabilities are exacerbated as AI projects increasingly rely on cloud infrastructure, where misconfigurations can lead to data breaches.
Prompt injection attacks target large language models (LLMs), where malicious prompts trick the AI into revealing confidential information or executing harmful actions. This is particularly risky for AI-integrated applications, like chatbots handling customer data.
Recent discussions on platforms like X highlight real-world concerns. For example, reports of Microsoft combating deepfakes and nation-state attacks underscore the global scale of these threats. Similarly, warnings about AI-driven threats to critical infrastructure emphasize the need for vigilance. Overall, these threats highlight a shift: only 10% of organizations are fully prepared, leaving most exposed.
Specific Risks to AI Projects
AI projects face unique risks due to their reliance on vast datasets, complex algorithms and interconnected ecosystems. Supply chain attacks are a major concern; third-party libraries or pre-trained models can harbor backdoors. For instance, a compromised dependency in an open-source AI framework could allow attackers to inject malware during model training.
Privacy risks arise from handling sensitive data. Model inversion can leak personal information, violating regulations like GDPR. In 2025, with AI processing petabytes of data, a single breach could expose millions of records.
Deployment environments add layers of vulnerability. Cloud-based AI projects are prone to misconfigurations, leading to unauthorized access. Edge AI, deployed on devices like IoT sensors, faces physical tampering risks.
Insider threats are amplified in AI contexts. Employees with access to models might inadvertently or maliciously compromise them. Misuse of AI tools within projects, such as unauthorized fine-tuning, can introduce biases or weaknesses.
Ethical and bias-related risks, while not purely cyber, intersect with security. Biased models can lead to discriminatory outcomes, inviting legal scrutiny and reputational damage. Projects must also contend with regulatory compliance, as new laws demand transparency in AI security practices.
Recent X posts illustrate these risks in action, such as discussions on AI’s role in detecting threats but also creating them.
Strategies to Protect Your AI Projects
Protecting AI projects demands a security-by-design approach, integrating defenses throughout the lifecycle. Start with secure data management: anonymize datasets, use encryption and implement access controls to prevent poisoning. Regularly audit data sources and employ techniques like differential privacy to safeguard sensitive information.
For model security, harden against adversarial attacks by training with robust datasets and using defensive distillation, where models learn from softened outputs to resist perturbations. Implement watermarking to detect model theft and use secure enclaves for inference to protect against inversion.
Adopt a Zero Trust architecture, verifying every access request. This is crucial for cloud-deployed AI, where identity and access management (IAM) should include multi-factor authentication and least-privilege principles. Continuous monitoring with AI-driven tools can detect anomalies in real-time, such as unusual query patterns indicating prompt injection.
Leverage AI for defense: machine learning can automate threat detection, analyzing vast data to spot unknown threats like zero-day exploits. Tools like user and entity behavior analytics (UEBA) profile normal activity and flag deviations. Generative AI can simulate attacks for testing defenses, predicting vulnerabilities.
Best practices include regular software updates to patch vulnerabilities and fostering a security culture through training. Develop incident response plans tailored to AI, including rollback mechanisms for poisoned models. Compliance with standards like SOC 2 ensures robust controls.
Integrate security into DevOps (SecDevOps) for continuous vulnerability scanning. Use ethical AI guidelines to mitigate bias risks. For phishing and deepfakes, AI-powered detection scans content for anomalies.
Future trends point to AI security agents automating responses, reducing human error. Organizations should collaborate, sharing threat intelligence to stay ahead.
Case Studies and Real-World Examples
Real-world incidents illustrate these threats and protections. In 2025, a major cloud provider suffered a data poisoning attack on its AI recommendation system, leading to manipulated outputs and user distrust. By implementing robust data validation and AI monitoring, they mitigated future risks.
Another case: A financial firm faced model inversion, exposing client data. Adopting encrypted training and Zero Trust prevented recurrence.
Microsoft’s efforts against deepfakes from Russia and China highlight proactive AI defenses. These examples show that early detection and resilient frameworks are key.
Conclusion
Cybersecurity threats in AI are escalating, but with strategic protections, projects can thrive securely. By addressing data poisoning, adversarial attacks and AI misuse through secure design, monitoring and AI defenses, organizations can build resilience. As AI evolves, so must our defenses—prioritizing governance, ethics and collaboration. In 2025, protecting AI isn’t just about technology; it’s about fostering trust in an AI-driven world. Stay vigilant, update practices and leverage resources like industry reports to safeguard your innovations.